Modern vehicles are no longer just mechanical machines—they’re complex, connected systems, constantly exchanging data with the outside world. From infotainment units to over-the-air updates and vehicle-to-cloud communication, connectivity has become a core part of the automotive experience.
But with increased connectivity comes increased exposure. Cyberattacks targeting vehicles are no longer theoretical—they’re real, and their consequences can impact safety, privacy, and system integrity.
This is where Threat Analysis and Risk Assessment (TARA) becomes essential. TARA provides a structured approach to identifying potential threats, analyzing vulnerabilities, and determining how those risks should be addressed during development. It’s not just a technical exercise—it’s a proactive process that helps prevent real-world attacks, such as remote manipulation of vehicle functions or unauthorized access to sensitive data.
Far from being just another compliance task, TARA is central to building secure, reliable vehicles that can withstand today’s evolving cybersecurity landscape. Ignoring it means leaving critical systems exposed. Applying it means building with security in mind—right from the start.
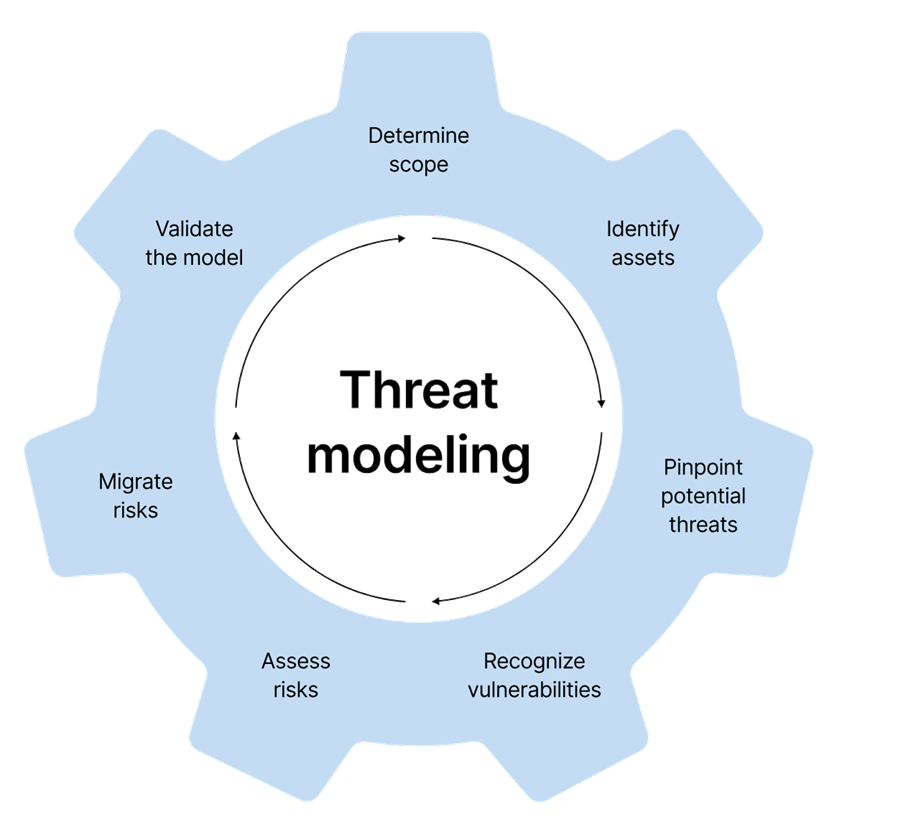
Breaking Down the TARA Process:
TARA is not a one-time activity—it’s a continuous process that evolves alongside new technologies, threat landscapes, and system updates. Just as your smartphone receives regular software patches to address security issues, vehicles require ongoing cybersecurity efforts to remain protected. TARA provides a structured, repeatable approach for identifying, evaluating, and mitigating potential threats and vulnerabilities throughout the vehicle lifecycle. It also ensures alignment with industry standards such as ISO/SAE 21434.
The process typically includes the following key steps:
1. Identifying Assets
The first step is to identify all critical components of the system—hardware, software, and communication interfaces—that may be exposed to cybersecurity threats.
2. Identifying Threats
Potential threats are then analyzed, ranging from remote cyberattacks to physical tampering. This step helps define what the system needs to be protected against.
3. Developing Threat Scenarios
Detailed attack scenarios are constructed using methods such as attack trees, capturing how a threat actor might exploit system vulnerabilities.
4. Assessing Impact
Each scenario is evaluated to understand the potential consequences of a successful attack, particularly in terms of safety, operational disruption, and data compromise.
5. Evaluating Likelihood
The feasibility of each threat scenario is estimated based on attacker capabilities, system exposure, and existing controls.
6. Calculating Risk
Risk is determined by combining impact and likelihood, helping prioritize which threats require the most attention and mitigation.
7. Defining Security Controls
Based on the identified risks, appropriate security requirements and countermeasures are defined to reduce or eliminate vulnerabilities.
8. Validating the Implementation
Security measures are tested and verified to ensure they effectively mitigate the targeted threats and align with the original risk assessment.
In today’s connected automotive landscape, cybersecurity isn’t just a technical requirement—it’s a matter of trust. Drivers rely on their vehicles not only for performance and comfort, but also for safety in an increasingly digital environment. That trust depends on the unseen systems working to protect every line of code and every data exchange.
Threat Analysis and Risk Assessment (TARA) is a foundational process in modern automotive development. It helps manufacturers identify where systems may be vulnerable, understand how those vulnerabilities could be exploited, and take the right steps to reduce risk—before a threat ever reaches the road.
TARA doesn’t make headlines, but it plays a critical role behind the scenes—shaping safer, more resilient vehicles from day one.